Hacking WIFI
WEP stands for Wired equivalent privacy and is an encryption technology that appeared in 1997. It is composed of a user-specified key (PSK) and an Initialization Vector (symmetric vector) made of the traffic key of the encryption algorithm RC4.
There are 64 bits in the encryption length, and 128 bits that appeared after the restrictions on the export of encryption technology in the United States were lifted, and IV was a fixed value of 24 bits.
The IV of plain text made of RC4 has a defect that the original text can be recovered by retrieving the encryption key when the packets of the same type are repeated and the sufficient number of packets is accumulated.
WPA improved this.
By increasing the length of the IV to 48 bits, we solved the shortcomings of the IV that is fixedly formed in the encryption algorithm to prevent the occurrence of duplicate values, reducing the possibility of hacking, and IEEE called TKIP (Temporal Key Integrity Protocol) and AES (Advanced Encryption Standard) It is said to have introduced the 802.11i security standard.
TKIP is an improvement on the existing WEP algorithm, and eliminates the vulnerability of exporting IV as it is from the cryptographic algorithm (RC4), and changed it to a method that encrypts and sends all data unlike the previous one.
AES encryption is added to the TKIP mixing process.
Here, TKIP is a compatible algorithm with existing WEP devices, and AES refers to encryption using standard AES symmetric key encryption.
A Wikipedia explanation of what AES is.
Hacking WIFI
WEP hacking is to analyze the pattern through IV collection and analysis to find the password, and there are many technologies and tools. If you search in Gugul, there are a lot of related contents. Typical hacking methods include Aircrack, wireshark, and commonview for wifi tools, and can be installed on Windows and Linux.
WPA is an improved version of WEP, and is an algorithm that fixes WEP's IV-related flaws. In general, we use dictionary assignment attacks.
Here, I hacked using windows 7 or 10, iptime usblan card, and commonview for wifi.
1. First, install commonview for wifi and aircrack_ng gui.
commonview for wifi
commonview for wifi
Go to https://www.tamos.com/download/main/ca.php and install it as instructed.
Go to Aircrack-Gui
https://sourceforge.net/projects/aircrack-ngwind/ and install it.
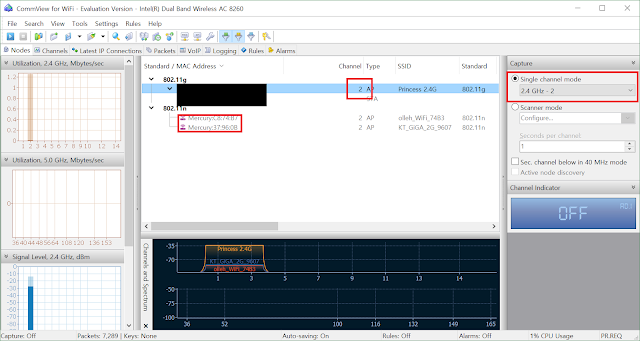
First, turn on commonview for wifi, and this screen will appear.
Go to Aircrack-Gui
https://sourceforge.net/projects/aircrack-ngwind/ and install it.
First, turn on commonview for wifi, and this screen will appear.

After checking the corresponding wifi channel number, set the channel in the single channel mode next to it and ring the run (the shape of the upper left arrow) to capture the packet.
The test version has a 5 minute timeout, but this is sufficient for dictionary password attacks using aircrack. PTW attack will have to collect more.
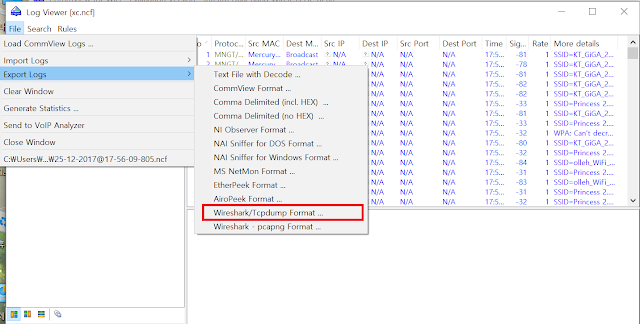
You can refer to this for merging packet files.
http://hump.tistory.com/3?category=709550 Open the file with the packet in the log viewer (just double-click it) and save it in wireshark format. If you do this, you have prepared the packet file. After that. Enter the aircrack installation path from here, and open the aircrack-ng-GUI and you will see a screen like this. Click WEP button for WEP hacking or click the button below for WPA hacking. There are two methods of attack using aircrack-ng: PTW attack and dictionary method. PTW attack is a method of attacking by analyzing the IV of WEP through a statistical method, and dictionary is a method of finding the password by randomly substituting the contents of the dictionary.
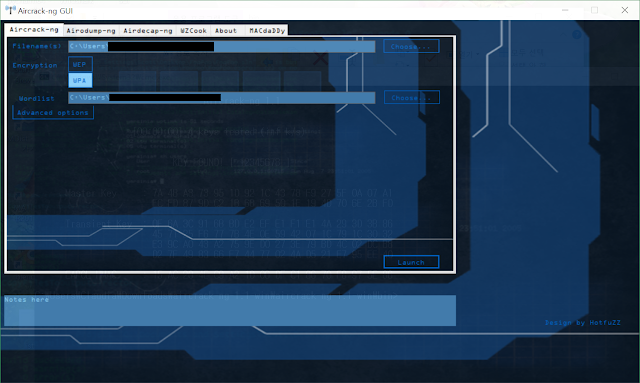
In the case of WPA, the password analysis is very complicated, so only the dictionary method is possible.
In the upper file input section, upload the packet log file converted to wireshark format.
In the lower part, you can upload a dictionary file.
You can download the dictionary file here or you can create your own in txt format at
http://www.wirelesshack.org/wpa-wpa2-word-list-dictionaries.html
.
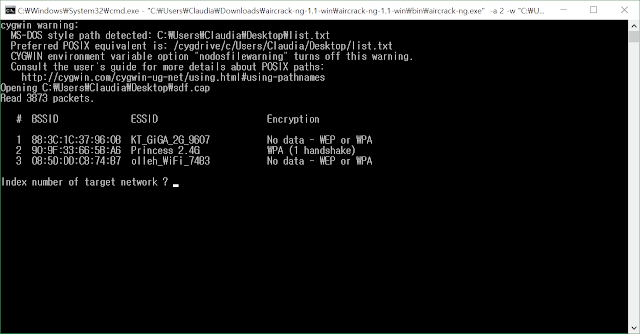
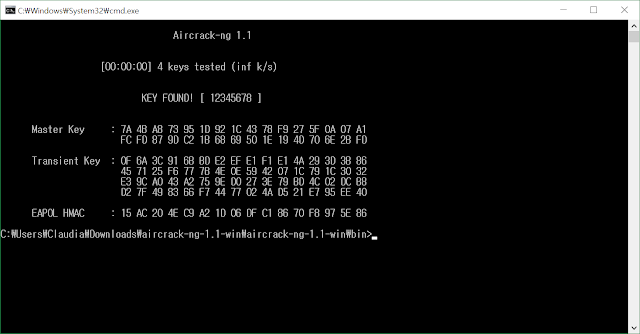
Once you press the WPA button and proceed to crack (Launch). You can select the applicable wWIFI here. You can proceed by pressing the number. Here, at least one WPA handshake is required to proceed. The handshake refers to the number of times the password between the WIFI and the device was transferred to each other, because the value is not known without the password itself being sent. If you have successfully performed all the above steps, wait a little while and the key will come out with the KEY FOUND message. If the key is simple, it comes out quickly, but if it is complicated, it can take a long time.
The test version has a 5 minute timeout, but this is sufficient for dictionary password attacks using aircrack. PTW attack will have to collect more.
You can refer to this for merging packet files.
http://hump.tistory.com/3?category=709550 Open the file with the packet in the log viewer (just double-click it) and save it in wireshark format. If you do this, you have prepared the packet file. After that. Enter the aircrack installation path from here, and open the aircrack-ng-GUI and you will see a screen like this. Click WEP button for WEP hacking or click the button below for WPA hacking. There are two methods of attack using aircrack-ng: PTW attack and dictionary method. PTW attack is a method of attacking by analyzing the IV of WEP through a statistical method, and dictionary is a method of finding the password by randomly substituting the contents of the dictionary.


In the case of WPA, the password analysis is very complicated, so only the dictionary method is possible.
In the upper file input section, upload the packet log file converted to wireshark format.
In the lower part, you can upload a dictionary file.
You can download the dictionary file here or you can create your own in txt format at
http://www.wirelesshack.org/wpa-wpa2-word-list-dictionaries.html
.
Once you press the WPA button and proceed to crack (Launch). You can select the applicable wWIFI here. You can proceed by pressing the number. Here, at least one WPA handshake is required to proceed. The handshake refers to the number of times the password between the WIFI and the device was transferred to each other, because the value is not known without the password itself being sent. If you have successfully performed all the above steps, wait a little while and the key will come out with the KEY FOUND message. If the key is simple, it comes out quickly, but if it is complicated, it can take a long time.


In addition, there are several WIFI hacking methods on the Internet.
There are many other wifi hatching methods on the Internet.
Also upload related blog links.
Also upload related blog links.
How to hack on Backtrack
Crack Wifi Hack Wifi Password
 Reviewed by Mohsin Rohan
on
May 15, 2020
Rating:
Reviewed by Mohsin Rohan
on
May 15, 2020
Rating:
 Reviewed by Mohsin Rohan
on
May 15, 2020
Rating:
Reviewed by Mohsin Rohan
on
May 15, 2020
Rating:





No comments: